Covenant has integrated Octane into its CI/CD pipeline, so every PR gets an automated security analysis. Initial code reviews surfaced multiple issues, detected bugs from complex cross-chain interactions, provided diff-ready fixes, and helped the team avoid extra audit rounds.
Covenant Secures Cross-Contract Credit Markets with Octane Integration
Covenant has integrated Octane into its CI/CD pipeline, so every PR gets an automated security analysis. Initial code reviews surfaced multiple issues, detected bugs from complex cross-chain interactions, provided diff-ready fixes, and helped the team avoid extra audit rounds.
Continuous Code Security
When Octane founder Gio and Covenant founder Alan Hampton first met, Covenant was searching for a security partner that could keep up with their pace of development. A solution that could help the team ship faster, tighten feedback loops, and surface real risks early.
Covenant’s codebase was complex, with deep composability and cross-contract interactions that traditional audits often struggled to model fully. Manual reviews were slow, and findings arrived after weeks of back-and-forth cycles. The team needed a security layer that could run alongside development, not behind it.
That’s where Octane came in. To put it to the test, Gio and Alan made a bet: if Octane could find a high or critical severity vulnerability in code that had already been audited, Covenant would make it their trusted pre-deployment security partner.
They didn’t have to wait long for an answer.
Meet Covenant
Covenant is DeFi’s liquid credit layer — a fully onchain marketplace that connects leverage users and yield seekers under transparent, verifiable rules. Its Latent Swap AMM automatically prices and balances markets without external liquidity providers, turning any onchain asset into fully backed leverage or predictable yield.
Building something this composable means orchestrating complex cross-contract interactions where even a small logic gap can cause systemic risk. To combine speed and safety, Covenant turned to Octane for continuous, automated security that detects subtle issues early in development.
“I’ve been deeply impressed by how Octane surfaces findings from complex cross-contract interactions. Integrating it into our CI/CD pipeline has been a huge unlock. We now catch issues in real time instead of waiting for a full audit cycle. It’s saved us weeks of time and significant costs by avoiding re-audit rounds. Octane has uncovered many vulnerabilities that manual audits on the same commit did not.”
– Alan Hampton, CEO at Covenant
Early Results for Covenant
Each time Covenant ran Octane, the findings validated why continuous, automated code analysis belongs in every modern security workflow, uncovering 2 Criticals and 37 additional High, Medium, and Low findings across multiple runs.
🛑 Authorization gap on `onBehalfOf` in redeem/swap (Severity: Critical)

The bet between Gio and Alan didn’t take long to pay off. On the first analysis, before being sent to formal auditing, Octane uncovered a critical vulnerability. This is the issue that brought the two teams together.
Bug: A missing caller-auth check let anyone call `redeem`/`swap` on behalf of another user, burn their synths, and route the market’s base token to their chosen `to` address.
Fix: Octane flagged the dangerous path and provided the fix: require `msg.sender == onBehalfOf` (or an approved operator) before any synth burn.
Result: The discovery saved Covenant weeks of back-and-forth with auditors and prevented an issue that could have allowed the theft of user funds and tokens.
🛑 Unrestricted external calls via `multicall` (Severity: Critical)
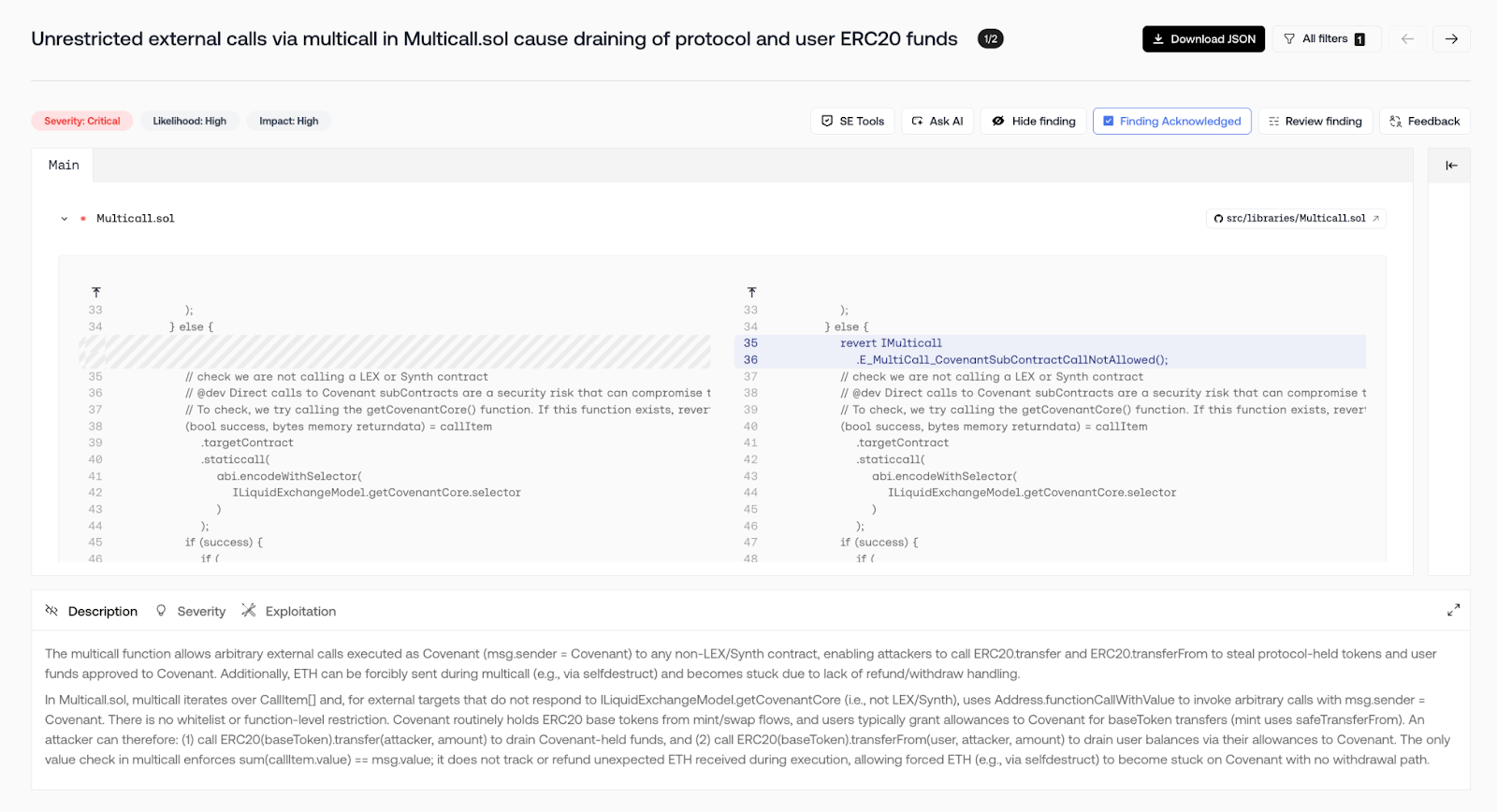
During a subsequent manual audit, Covenant ran Octane to review code changes before sending them back to the auditor. Octane uncovered a critical flaw in the way Covenant.sol both custodies base tokens and accrued protocol fees and inherits a permissive `Multicall`. By tracing execution with Covenant as `msg.sender`, Octane showed that an attacker could chain external calls across contracts with Covenant’s authority.
Bug: A permissive `multicall` function lets anyone execute arbitrary external calls as Covenant. Since Covenant is the onchain holder of the base token reserves and the protocol’s accrued fee balance, an attacker can invoke ERC-20 methods like `transfer`, `transferFrom`, or first `approve` then `transferFrom`, with `msg.sender == Covenant`. This enables direct theft of base tokens and accumulated protocol fees from Covenant’s balances—no allowance or user signature required.
Fix: Octane recommended only allowing `multicall` targets that are trusted LEX/synth contracts (or on an explicit allowlist), ban calls to raw ERC-20 logic (or block `transfer`/`transferFrom` selectors), and require caller/operator authorization for any state-changing external calls.
Result: With Octane analyzing complex interactions between inherited and composable contracts, this finding eliminated audit rounds, shortened remediation time, and protected both protocol and user funds.
🟡 Zero-value edge in debt math could freeze a market (Severity: Medium)

In a later analysis, this edgecase was identified by Octane and enabled Covenant to level up their security coverage.
Bug: A zero-handling bug in `_calculateMarketState` could freeze a market. When liquidity is very low, `computeMaxDebt` can floor to 0, which either sets `debtDexRatioX96` to 0 or divides by zero. The market flips to under-collateralized and most actions block, effectively trapping funds.
Fix: Octane recommended explicit zero guards. If `maxDebtValue == 0`, derive the ratio from the last debt notional price instead of `0/zSupply`; if `zTokenSupply == 0`, skip the ratio update and set `underCollateralized` only when there’s non-zero debt. This keeps pricing well-defined and preserves a recovery path out of under-collateralization.
Result: With Octane running continuously, Covenant maintains full visibility and protection across evolving codebases for maximum security coverage.
Bet On Security With Octane
After integrating Octane, Covenant didn’t just harden its codebase. It changed how the team builds. Security became part of development itself: fast, automated, and continuous.
With Octane integrated, Covenant gained:
- Continuous security with severity prioritization, exploit paths, and suggested diffs
- Automated reviews that run on every PR for consistent checks as code evolves
- Real-time detection that saves time and money by catching issues early in development
- Deep visibility that uncovers vulnerabilities in complex cross-contract interactions
All of this runs directly in CI/CD. For Covenant, shifting security left shortened audit cycles, reduced feedback loops, and increased confidence in every release.
Ready to make your own bet on security? Schedule a demo today to see what Octane can do for you.




